This is a similar topic to the one about Risk Assessment Methodologies, but the difference here is that we are focusing on the complete way to prevent and mitigate risk in the IT department.
The main framework is pretty much this:
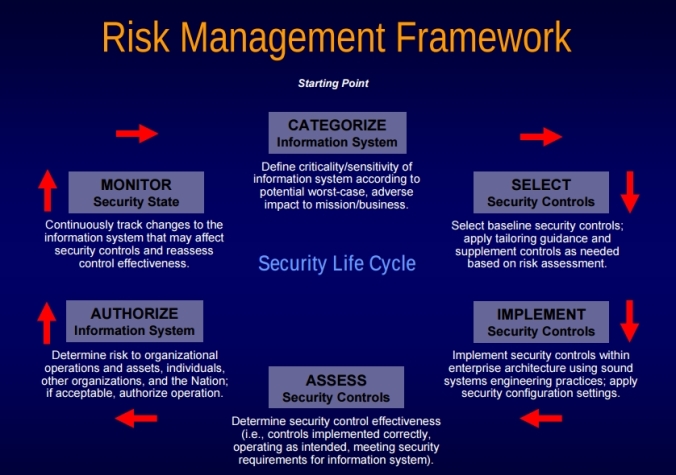
Step 1: Categorize
Categorize the information system and the information processed, stored, and transmitted by that system based on an impact analysis.
Step 2: Select
Select an initial set of baseline security controls for the information system based on the security categorization; tailoring and supplementing the security control baseline as needed based on organization assessment of risk and local conditions.
Step 3: Implement
Implement the security controls and document how the controls are deployed within the information system and environment of operation.
Step 4: Assess
Assess the security controls using appropriate procedures to determine the extent to which the controls are implemented correctly, operating as intended, and producing the desired outcome with respect to meeting the security requirements for the system.
Step 5: Authorize
Authorize information system operation based upon a determination of the risk to organizational operations and assets, individuals, other organizations and the Nation resulting from the operation of the information system and the decision that this risk is acceptable.
Step 6: Monitor
Monitor and assess selected security controls in the information system on an ongoing basis including assessing security control effectiveness, documenting changes to the system or environment of operation, conducting security impact analyses of the associated changes, and reporting the security state of the system to appropriate organizational officials.
For more information about this, you can take a look at a document here. Or you can go to the NIST-RMF Overview and go as deep as you may want to go.
For now, that’s it, but as always, good day, good luck, be safe, eat well, move your ass at the gym or somewhere else, take your vitamins, talk to interesting people, don’t text and drive, have enough sex (even if it has to be with yourself), learn things, share things and try to make the world a better place, move on on achieving your definition of “success” and drink more coffee!




